A partial replacement for PGP/GPG
Command Line – Modern File Encryption

© Lead Image © photonphoto, 123RF.com
Age, a modern encryption tool, could soon replace PGP and GPG when it comes to file encryption.
If you encrypt, you are probably familiar with Pretty Good Privacy (PGP) [1] or its clone GNU Privacy Guard (GPG). Most likely, you have used one of these tools to generate public and private keys and to encrypt email and files. The Free Software Foundation explains these tools in its Email Self-Defense Guide as a first step towards privacy [2]. However, despite PGP and GPS being ubiquitous when it comes to privacy, some people believe that these tools are counter-productive and little more effective than the feeble default protection available for PDF files when it comes to modern computing. Ironically, as PGP and GPG become more widely used, some security experts are advocating for their replacement with Actual Good Encryption (age), at least for file encryption [3].
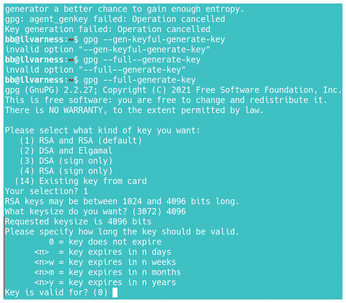
Why do some security experts claim that PGP and GPG are obsolete? To begin with, PGP and GPG have long public keys that can be difficult to work with when space is limited, and copying them accurately by hand is difficult. In particular, they can be difficult to configure, even when the simple configuration wizard is used (Figure 1). When generating a key, PGP and GPG require numerous choices, including the encryption method, the key size, and how long the key is valid. Even a moderately skilled user can be hard-pressed to answer such questions intelligently. As a result, users may simply fall back on the defaults, although ignorance and security are hardly compatible. Many users, too, complain about having to move the cursor around to generate sufficient randomness – and, the longer the key, the longer it takes to generate the randomness. To further add to the confusion, PGP and GPG do too many things, such as signing services and key management, that many users have no interest in, which can add to the confusion.
[...]
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
KDE Linux Alpha Available for Daring Users
It's official, KDE Linux has arrived, but it's not quite ready for prime time.
-
AMD Initiates Graphics Driver Updates for Linux Kernel 6.18
This new AMD update focuses on power management, display handling, and hardware support for Radeon GPUs.
-
AerynOS Alpha Release Available
With a choice of several desktop environments, AerynOS 2025.08 is almost ready to be your next operating system.
-
AUR Repository Still Under DDoS Attack
Arch User Repository continues to be under a DDoS attack that has been going on for more than two weeks.
-
RingReaper Malware Poses Danger to Linux Systems
A new kind of malware exploits modern Linux kernels for I/O operations.
-
Happy Birthday, Linux
On August 25, Linux officially turns 34.
-
VirtualBox 7.2 Has Arrived
With early support for Linux kernel 6.17 and other new additions, VirtualBox 7.2 is a must-update for users.
-
Linux Mint 22.2 Beta Available for Testing
Some interesting new additions and improvements are coming to Linux Mint. Check out the Linux Mint 22.2 Beta to give it a test run.
-
Debian 13.0 Officially Released
After two years of development, the latest iteration of Debian is now available with plenty of under-the-hood improvements.
-
Upcoming Changes for MXLinux
MXLinux 25 has plenty in store to please all types of users.