Protecting your private key with the OpenPGP smartcard
Card Games

Improve communication security with GnuPG and the OpenPGP smartcard.
Gnu Privacy Guard [1] (sometimes called GnuPG or just GPG) has long served the open source community as a tool for encrypting email and other documents. GnuPG, which is based on the OpenPGP standard, uses the familiar asymmetric key exchange approach, with a public key to encrypt the message and a private key to decrypt it. The public key is shared with other users, and the private key is kept secret by the message receiver. As long as no one discovers the private key, only the message receiver will be able to read the message.
GnuPG is thus a powerful tool for ensuring confidential communication – as long as the private key stays private. But protecting a private key is not as easy as it sounds. If you store the private key on your computer, the key is only as safe as your computer is. Your system could fall victim to malware, cyber attack, or a nosy system administrator, and if so, the private key would be at risk. On the other hand, if you are a mobile worker and you have the need to use the private key from multiple locations, lugging it around on a thumb drive poses a whole different set of security issues.
One solution that is gaining momentum is to carry the private key on a smartcard. The ISO/IEC 7816-4 standard defines a method for encoding cryptographic keys on a smartcard. The OpenPGP smartcard is an implementation of ISO/IEC 7816-4 for GnuPG and other OpenPGP-compatible encryption systems.
Smartcard and Card Reader
If you want to get started with the OpenPGP smartcard, the first step is to purchase the necessary hardware and software. You can obtain the smartcard (Figure 1), which is currently version 3.4, from several online outlets [2] for around EUR20. To work with the smartcard, you also need a card reader. Basically, any model that can handle contact smartcards is suitable. Some card readers have an integrated keyboard, which means you can enter the PIN of the card directly on the reader. If you enter the PIN directly on the reader, you avoid the possibility of it being sniffed when you type it at the keyboard.
The next step is to install the required software. Communication with a card reader relies on the CCID protocol [3]. The CCID protocol (short for "Chip Card Interface Device") facilitates communication between a USB chip card reader and a PC via a uniform interface.
Download the current version of the CCID software, which was 1.4.33 at the time of this article, and unpack the archive in the shell with the tar xfvj ccid-1.4.33.tar.bz2 command. Then change to the directory where you unpacked the files and execute the commands from Listing 1.
Listing 1
Compiling
./configure make sudo make install
Separate packages are also available for different distributions. On Ubuntu, you can alternatively use the command from Listing 2, Line 1 for the install. For some card readers, it happens that you need an additional driver. Some other card readers do not need any additional software beyond the standard driver and are ready to use immediately after plugging in [4].
Listing 2
Installing on Ubuntu
01 sudo apt install libccid 02 sudo apt install pcscd 03 sudo apt install pcsc-tools 04 sudo apt install gnupg2 05 sudo apt install gpa
The PC/SC standard provides the interface to the smart card reader. In the Linux world, PC/SC Lite [5] is a good tool for the interface. Download the program from the project page. Unpack the current version 1.9 in the shell by typing tar xfvj pcsc-lite-1.9.0.tar.bz2. Then change to the directory where you unpacked the files and execute the commands from Listing 1. Depending on the distribution, you can alternatively install the program via the package manager (Listing 2).
The PCSC Tools [6] let you test whether the card reader is installed correctly and whether it detects the smartcard correctly. You can download PCSC Tools from the project website. Unpack the archive in the shell by typing tar xfvj pcsc-tools-1.5.7.tar.bz2. In this case, too, you need to build the program from the archive you unpacked at the command line with the usual three steps (Listing 1). Alternatively, you can install the program from the package sources; on Ubuntu, Listing 2 Line 3 handles the installation.
Once you have connected a card reader to the system and installed the required software, run the pcsc_scan command in the shell to test if the device works correctly. Insert your smartcard into the card reader. If the device displays it as OpenPGP Card V3 (as shown in Figure 2), the card and reader are ready for use.
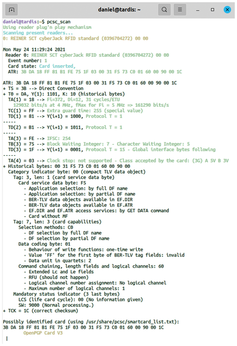 Figure 2: The pcsc_scan command detects a card reader of type "REINER SCT CyberJack RFID Standard" with an OpenPGP card inserted.
Figure 2: The pcsc_scan command detects a card reader of type "REINER SCT CyberJack RFID Standard" with an OpenPGP card inserted.
Before you start, make sure GnuPG [7] is in place. The current version is 2.3.1 (see the box entitled "Current GPG"). After downloading the current version, unpack the archive via the shell with the tar xfvj gnupg-2.3.1.tar.bz2 command. Then change to the directory where you unzipped the files and run the three build steps (Listing 1). On Ubuntu, you could alternatively use the command from Listing 2, Line 4. You can also install GnuPG through your distro's package manager.
Current GPG
Make sure you install the latest version of GnuPG, but in any case, avoid everything from the deprecated 1.x branch. On older distributions, you may only have this outdated version in the package sources. You can check the installed version in the shell with the gpg --version command.
Version 1.x and version 2.x can be installed side by side. In this article, the gpg command is used when working with GnuPG. If you are not sure whether an outdated version is still installed in parallel, use the gpg2 command instead. This command will ensure that you are always working with version 2.
If you prefer to use GnuPG via a graphical user interface, the GNU Privacy Assistant is a good choice. You can install the program via your distribution's package manager. On Ubuntu, use the command from Listing 2, Line 5.
After the installation, you will find a launcher in the application menus. Alternatively, you can call up the tool with the gpa command in a terminal. Then set up your smartcard via the Window | Card Management menu.
Set Up OpenPGP Smartcard
Once you have obtained the necessary hardware and installed the required software, the next step is to set up your new OpenPGP smartcard. Insert the card into the card reader and execute the gpg --card-status command. The output should look like Figure 3. The empty card now needs to be populated.
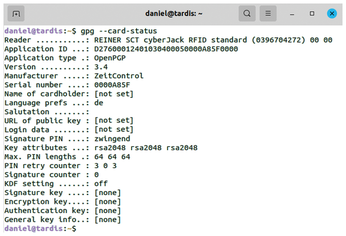 Figure 3: The [none] in the last four lines of the output of gpg --card-status shows that the card does not yet contain any keys.
Figure 3: The [none] in the last four lines of the output of gpg --card-status shows that the card does not yet contain any keys.
You can edit the data stored on the card with gpg --card-edit. The output from the command first shows you the current contents of the card. After that, you will see the gpg/card> prompt, which is waiting for commands to edit the OpenPGP smart card. Type admin to start editing the card. Then type help to get an overview of the possible commands.
The first thing to do is to change the PIN and the admin PIN of the card by typing passwd at the GPG prompt. If you choose 1 – change PIN in the selection menu, the software will first ask for the old PIN for the card. The preset default PIN is 123456. You can then type a new PIN. If you have chosen a card reader with an integrated keyboard, input the PIN via the keys on the reader.
If you enter the PIN incorrectly three times in a row when using the card, the smartcard is blocked. In this case, you can unlock the card with the unblock command in the Admin menu. You will need the Admin PIN to unblock the PIN; you can set up the Admin PIN using the same approach as the normal PIN.
To do so, select 3 – change Admin PIN from the PIN menu. The preset default Admin PIN is 12345678. Entering the Admin PIN incorrectly three times in a row when using the card will permanently lock the card. Once you have successfully changed both PINs, exit the PIN menu again via the menu item Q – quit.
You can individualize your OpenPGP smartcard by saving your name with the name command and your salutation with the salutation command at the GPG prompt. The lang command lets you set a different language.
On the Card
After setting up the OpenPGP smartcard, it is time to create a new key. You can generate the key directly on the OpenPGP smartcard with the generate command. The first thing you need to decide is whether you want to store a backup copy of the new key pair outside the card. This is usually a good idea because otherwise the key pair will be irretrievably lost if the card stops working. Confirm the prompt by pressing Y. After that, the software will ask for the PIN you just set.
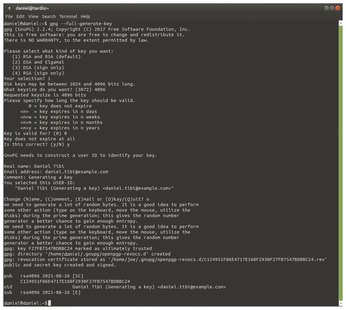
Next, decide how long the new key is valid. If you never want the key to expire, type 0. Then enter your name and e-mail address and set a password for the key. To compute the key, the system uses random data that it generates based on the activity on the computer. It is a good idea to move the mouse and press various keys while the key is being generated (Figure 4). In the test, the system needed only a few seconds to create the key. Your new key is then ready for use.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Systemd Fixes Bug While Facing New Challenger in GNU Shepherd
The systemd developers have fixed a really nasty bug amid the release of the new GNU Shepherd init system.
-
AlmaLinux 10.0 Beta Released
The AlmaLinux OS Foundation has announced the availability of AlmaLinux 10.0 Beta ("Purple Lion") for all supported devices with significant changes.
-
Gnome 47.2 Now Available
Gnome 47.2 is now available for general use but don't expect much in the way of newness, as this is all about improvements and bug fixes.
-
Latest Cinnamon Desktop Releases with a Bold New Look
Just in time for the holidays, the developer of the Cinnamon desktop has shipped a new release to help spice up your eggnog with new features and a new look.
-
Armbian 24.11 Released with Expanded Hardware Support
If you've been waiting for Armbian to support OrangePi 5 Max and Radxa ROCK 5B+, the wait is over.
-
SUSE Renames Several Products for Better Name Recognition
SUSE has been a very powerful player in the European market, but it knows it must branch out to gain serious traction. Will a name change do the trick?
-
ESET Discovers New Linux Malware
WolfsBane is an all-in-one malware that has hit the Linux operating system and includes a dropper, a launcher, and a backdoor.
-
New Linux Kernel Patch Allows Forcing a CPU Mitigation
Even when CPU mitigations can consume precious CPU cycles, it might not be a bad idea to allow users to enable them, even if your machine isn't vulnerable.
-
Red Hat Enterprise Linux 9.5 Released
Notify your friends, loved ones, and colleagues that the latest version of RHEL is available with plenty of enhancements.
-
Linux Sees Massive Performance Increase from a Single Line of Code
With one line of code, Intel was able to increase the performance of the Linux kernel by 4,000 percent.