Subgraph
Security Meets Accessibility
BySubgraph OS is designed with built-in, accessible security features and a modern desktop.
In graph theory, a subgraph is a graph contained by a larger graph. Inspired by efforts to apply graph theory to reverse engineering by comparing flow control graphs, Subgraph is a Montreal-based company and the name of the Linux distribution it is developing to make increased security easily available.
Many of Subgraph’s core members first met in the Calgary hacking scene in the 1990s. Another was a founder of the hacker space movement in Montreal. CTO Bruce Leidl is known for his work on Obfusated SSH, a technology used in Tor and Psiphon3.
Two core members, president David Mirza Ahmad and principal developer David McKinney, were moderators of Bugtraq, the controversial mailing list that advocates the free sharing of vulnerability details and exploit code – an approach that many proprietary companies often oppose, preferring to keep vulnerabilities secret until they can be patched.
“System operators were being compromised and, facing negligent software vendors, [they] took matters into their own hands,” Ahmad says, describing Bugtraq around the turn of the millennium. “Bugtraq was also a place to post interesting computer security research, including early implementations of new ideas.” Much of this work used free software licenses, partly because subscribers were understandably reluctant to run a binary downloaded from a mailing list, but also because of what Ahmad describes as “the fantastic spirit of open collaboration” that developed among list regulars. The result, Ahmad says, was “tools and an opportunity to learn and explore that I could never have had any other way.”
As a result of these backgrounds, members of Subgraph pride themselves on being able to work at all levels, from low-level kernel code to Gnome Shell plugins to increase usability. Meant to be at least a 10-year project, Subgraph was originally founded in 2010 as an attempt to build a security business based on free software. “We did not want to work for boring proprietary software companies,” Ahmad says.
Its first product was Vega, a web application vulnerability scanner written in Java. It was followed by Orchid, a Java implementation of Tor. However, although both Vega and Orchid remain in use today, in 2013, Subgraph shifted its focus to privacy and security and began development of Subgraph OS. Currently in alpha release, Subgraph OS is intended as “a usable desktop that is resistant to an adversary armed with reliable exploits,” Ahmad says.
Another major goal is to make security easy to use. According to Ahmad, for example, “before Subgraph OS, many users had to build their own kernel to benefit from grsecurity and PaX,” two leading kernel security patches. A particular problem is managing these patches during system updates, which Subgraph OS automatically manages. Similarly, OnionShare, A Nautilus plugin developed by Subgraph’s Micah F. Lee, uses Tor services to share files securely and anonymously, and many applications are automatically sandboxed.
First Line Defenses
Subgraph is a Debian derivative running a Gnome desktop. Debian, Ahmad says, was chosen for its packaging and distro tool set and out of admiration for its community ideals. However, although based on these standard components, Subgraph OS includes substantial changes.
 Subgraph OS is one of the first distributions to make security features accessible from the desktop.
Subgraph OS is one of the first distributions to make security features accessible from the desktop.
To start, Subgraph’s kernel is compiled without support for obscure hardware, protocols, and unprivileged user namespaces. The result is that would-be intruders have fewer avenues of attack.
Additionally, Subgraph makes full use of kernel patches such as grsecurity, PaX, and RAP. Although RAP is a commercial product, in its kernel compilation, Subgraph uses a public demo of RAP that was made by PaX, giving free software users security to which they would otherwise not have access.
These patches “strive to be general and broadly useful mitigations that eliminate entire classes of vulnerabilities, rather than fixing individual instances,” Ahmad says. Their flexibility often makes them effective against newer, unannounced expoits – so-called zero-day vulnerabilities. Grsecurity and PaX also offer general hardening measures, including PID randomization, detection of brute force attacks, and the strengthening of chroots, whereas RAP is a modern defense against code reuse attacks, in which intruders take advantage of software vulnerabilities on an already compromised machine.
Similarly, Subgraph OS writes most of its own code in GoLang, a memory-safe language that guards against attacks that depend on memory corruption, such as buffer overflows. “It’s an interesting choice,” Ahmad remarks, “and fun to program in, especially if C has your heart” – a reference to the fact that both C and C+ have been historically open to memory vulnerabilities.
Second Line Defenses
Behind these defenses, Subgraph OS has additional defenses that are more visible to users. For example, the instant messenger Pidgin, which Adhmad dismisses as “suspected by many of having unpatched security vulnerabilities [and] written in an unsafe language,” has been replaced with CoyIM, written with the help of ThoughtWorks. Similarly, a feature called USBLockout removes an obvious vulnerability by controlling access to USB ports when the desktop is locked. Still to come are a system event monitor and notification system that alerts users to problems and Subgraph Mail, a replacement for Thunderbird. For now, the distribution ships with Enigmail ready to install, to make encrypted email easy to configure.
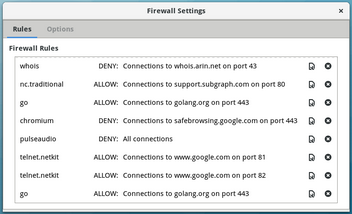
Another second line of defense is the Subgraph Firewall. Describing it as similar to Mac OS’s popular Little Snitch, Ahmad describes the Subgraph Firewall as allowing “users to better understand and control how individual applications communicate with servers on the Internet. As an example, during development, we found that the Gnome Calculator makes connections to hosts on the Internet when it is started. Although the connection is fairly benign (IMF and Europenan Central Bank, to obtain curency conversion rates), it was default behavior, and we found that surprising.” To the best of Ahmad’s knowledge, Linux currently has nothing comparable.
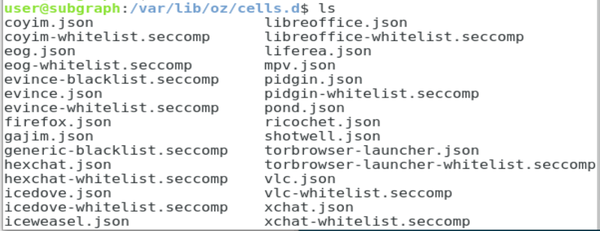
However, Subgraph’s most important innovation on the desktop is Oz, its sandboxing system. Based on existing technologies, Oz is unique in its strict filtering of system calls. Ahmad estimates that Subgraph’s desktop applications average about one-third the number of system calls they do in other distributions. Each application has its own profile for Oz, which is stored in an editable file, /var/lib/oz/cell.d.
The roadmap for Oz also includes the ability to restrict outgoing access within sandboxes and certificate pinning, which double-checks server certificates against a set of hashes of public keys for the server name. Essentially, with Oz, Subgraph can offer much more security customization for individual applications than other sandboxes.
All these tools will be built in to the desktop, making them easy to access. In the alpha release, for example, an application in the upper left corner of the panel lists all applications that are currently running using Oz.
Continuing Development
Subgraph OS is an ambitious project and still some ways from general completion. Ahmad expects the beta release in six months and the general release in a year. However, Subgraph particularly wants to ship with full Wayland support, which may cause some delay, and the full implementation of some features may extend beyond the 1.0 release.
However, judging from the alpha release, Subgraph promises not only to have unique security features, but also to make them accessible. In fact, except perhaps for Qubes OS, which takes a very different approach to accessible security, I know of no other distribution that integrates security features so thoroughly into the desktop. In these days of increasingly urgent calls for accessible security, Subgraph shows every sign of becoming a major player in the near future.
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
TrueNAS 25.04 Arrives with Thousands of Changes
One of the most popular Linux-based NAS solutions has rolled out the latest edition, based on Ubuntu 25.04.
-
Fedora 42 Available with Two New Spins
The latest release from the Fedora Project includes the usual updates, a new kernel, an official KDE Plasma spin, and a new System76 spin.
-
So Long, ArcoLinux
The ArcoLinux distribution is the latest Linux distribution to shut down.
-
What Open Source Pros Look for in a Job Role
Learn what professionals in technical and non-technical roles say is most important when seeking a new position.
-
Asahi Linux Runs into Issues with M4 Support
Due to Apple Silicon changes, the Asahi Linux project is at odds with adding support for the M4 chips.
-
Plasma 6.3.4 Now Available
Although not a major release, Plasma 6.3.4 does fix some bugs and offer a subtle change for the Plasma sidebar.
-
Linux Kernel 6.15 First Release Candidate Now Available
Linux Torvalds has announced that the release candidate for the final release of the Linux 6.15 series is now available.
-
Akamai Will Host kernel.org
The organization dedicated to cloud-based solutions has agreed to host kernel.org to deliver long-term stability for the development team.
-
Linux Kernel 6.14 Released
The latest Linux kernel has arrived with extra Rust support and more.
-
EndeavorOS Mercury Neo Available
A new release from the EndeavorOS team ships with Plasma 6.3 and other goodies.